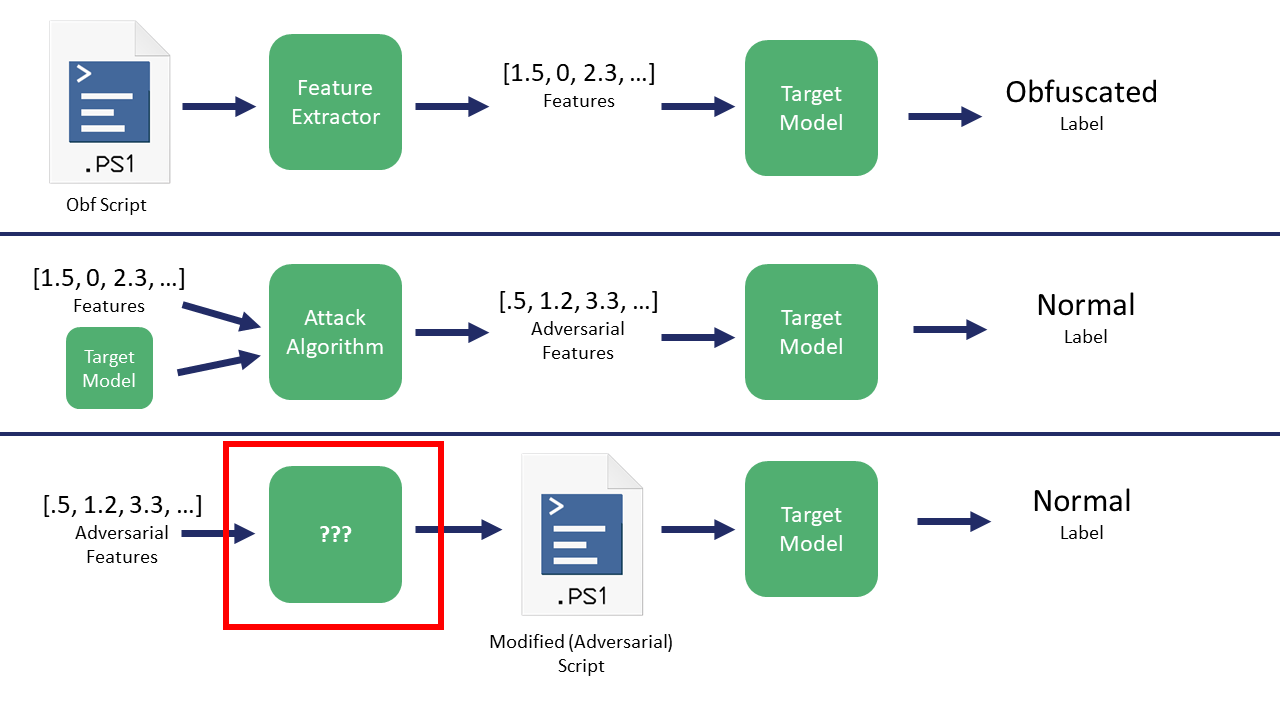
Black Box Attack Watches inputs and outputs Controls input text ... | Download Scientific Diagram

Sensors | Free Full-Text | A Distributed Black-Box Adversarial Attack Based on Multi-Group Particle Swarm Optimization
Architecture overview of distributed black-box adversarial attack using... | Download Scientific Diagram
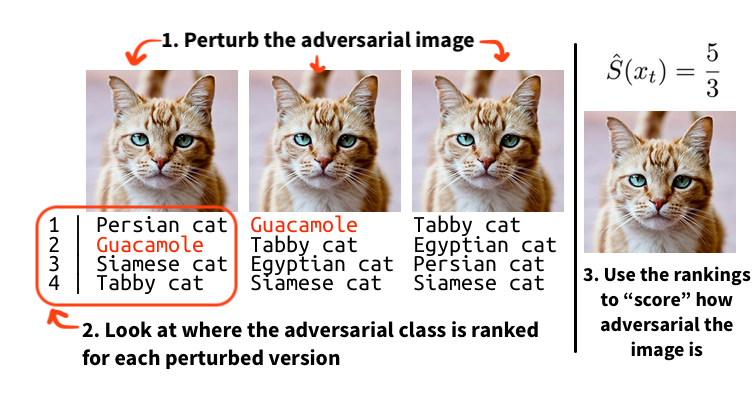
Institute for Applied AI - Selected Topics in Deep Learning - #1 Adversarial Attacks: C3 Black-Box Attacks
![PDF] Perceptual Quality-preserving Black-Box Attack against Deep Learning Image Classifiers | Semantic Scholar PDF] Perceptual Quality-preserving Black-Box Attack against Deep Learning Image Classifiers | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3ec44bdf77b2d5b5e480365aff5a8e9e0fa9242e/6-Figure3-1.png)
PDF] Perceptual Quality-preserving Black-Box Attack against Deep Learning Image Classifiers | Semantic Scholar
ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models

FE-DaST: Fast and effective data-free substitute training for black-box adversarial attacks - ScienceDirect