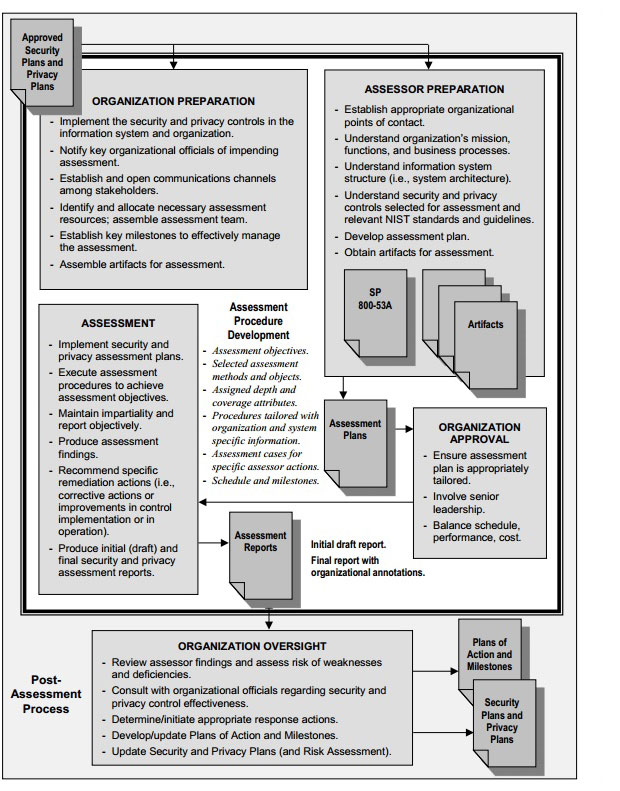
![PDF] Assessing Security and Privacy Controls in Federal Information Systems and Organizations: Building Effective Assessment Plans | Semantic Scholar PDF] Assessing Security and Privacy Controls in Federal Information Systems and Organizations: Building Effective Assessment Plans | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/8461b9064ed42107994cd56985f04f9ae865ec34/26-Figure1-1.png)
PDF] Assessing Security and Privacy Controls in Federal Information Systems and Organizations: Building Effective Assessment Plans | Semantic Scholar
Security Control Assessment Ppt Powerpoint Presentation Pictures Sample Cpb | Presentation Graphics | Presentation PowerPoint Example | Slide Templates

Information Security Assessment by Wentz Wu, CISSP/ISSMP/ISSAP/ISSEP,CCSP,CSSLP,CISM,PMP,CBAPWentz Wu