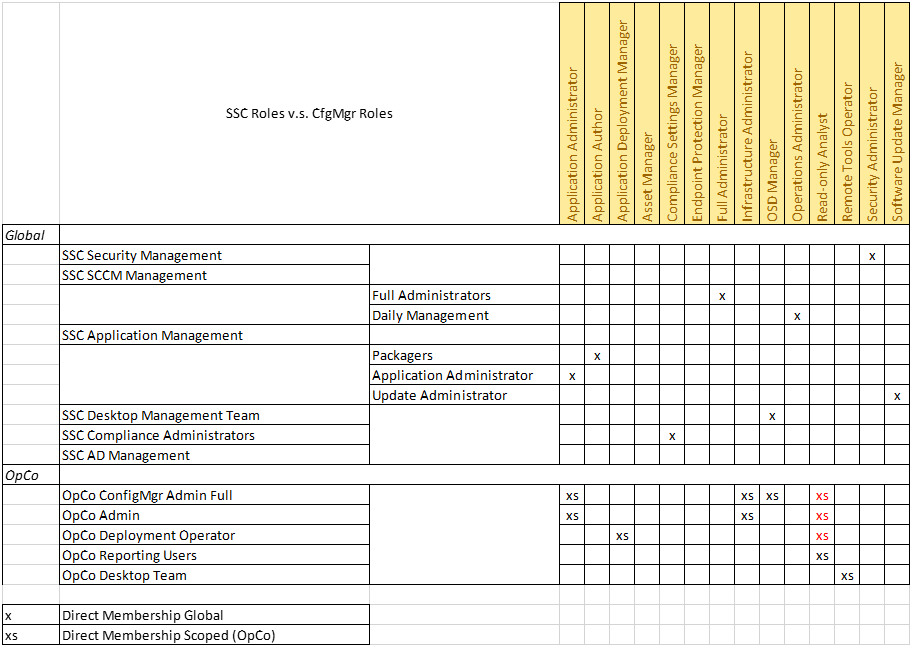
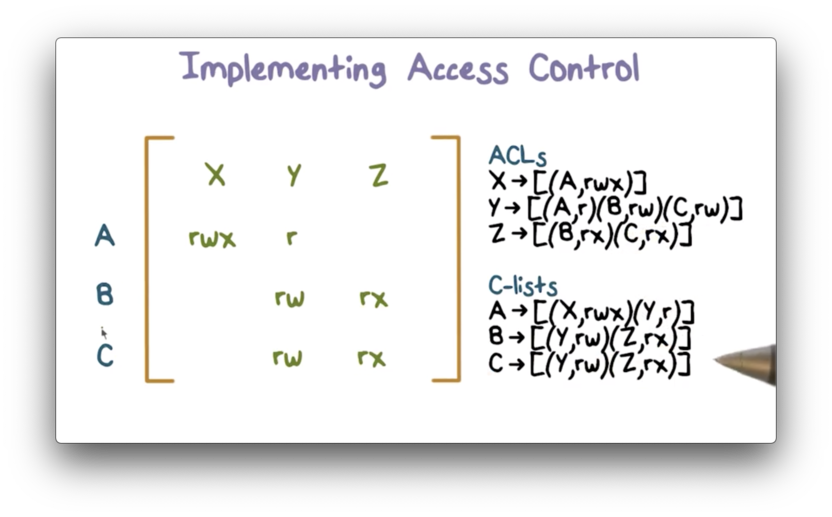
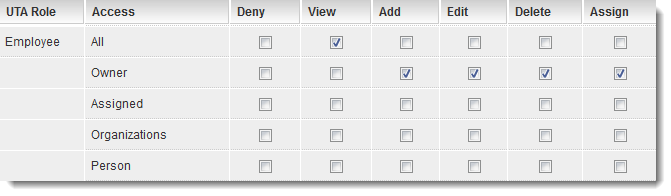
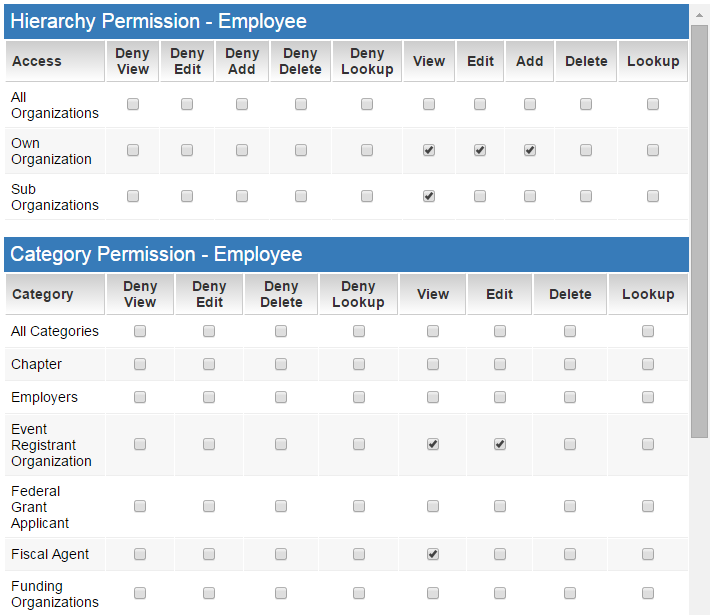
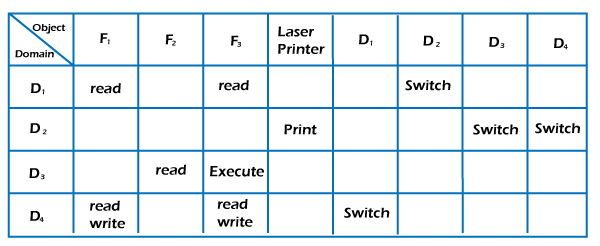
CISSP Domain 3 Security Engineering – Part 1 – Security Architecture Cheat Sheet – Page 2 – NAT OVERLOAD

1. An access control matrix, and its access control list and capability... | Download Scientific Diagram

1. An access control matrix, and its access control list and capability... | Download Scientific Diagram

IP 2 DM access control matrix for each role: User, LAG DBA and Server... | Download Scientific Diagram